What is single sign-on (SSO)?

Single sign-on, often known as SSO, is a session and user authentication service that enables users to access different apps with a single login credential, such as a name and password. SSO may be used by companies, smaller organizations, and even individuals to simplify the maintenance of multiple identities and passwords for numerous online accounts.
A simple web SSO service’s agent module on the application server gets a user’s particular authentication credentials from a specialized SSO policy server and authenticates the user against a user repository, such as an LDAP directory. This is done while the user is being authenticated against the user repository. The service verifies the end user’s identity across all of the apps to which the user has been granted access, and it prevents other password prompts from appearing for individual applications while they are being used simultaneously.
How single sign-on works
Single sign-on is an identity federation system that uses federated identity management (FIM). OAuth, pronounced “oh-auth,” allows third-party services like Facebook to utilize an end user’s account information without revealing their password.
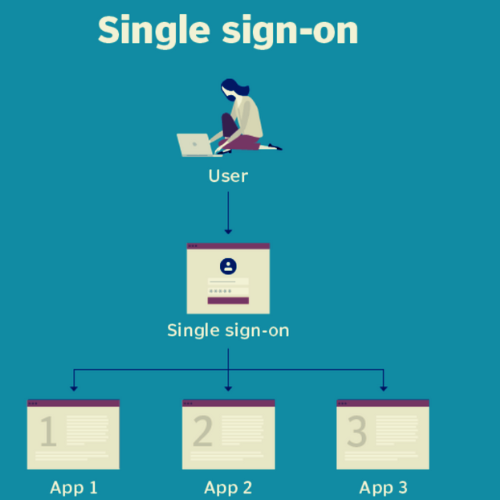
This diagram illustrates a single sign-on.
By supplying the service with an access token that contains the user’s authorization for certain account information to be shared, OAuth fulfils the role of an intermediary on the user’s behalf. When a user seeks to access an application provided by the service provider, the identity provider will get a request for authentication from the service provider. The service provider will then check the authentication, after which the user will be logged in.
Types of SSO configurations
Kerberos and SAML are used by several SSO services (SAML).
- SAML allows secure domains to communicate user authentication and authorization data via XML. SAML-based SSO involves user, identity provider, and service provider interactions.
- After providing credentials, Kerberos issues a ticket-granting ticket (TGT). The TGT retrieves service tickets for other apps without requiring reauthentication.
- Smart card-based SSO requires first-time logins using a card containing sign-in credentials. The card saves usernames and passwords. SSO smart cards contain certificates or passwords.
Security risks and SSO
Users will enjoy single sign-on simplicity, but the company’s security will be compromised. If an adversary is successful in obtaining possession of a user’s SSO credentials, that adversary will be given access to every application to which the user has permission, which will increase the amount of possible harm. It is necessary for each component of the SSO implementation to be paired with identity governance to prevent unauthorized access of any kind. Improved security may also be achieved by combining single sign-on (SSO) with either two-factor authentication (2FA) or multifactor authentication (MFA) for organizations.
Social SSO
SSO services from Google, LinkedIn, Twitter, and Facebook let users log in to third-party apps using their social network credentials. Social single sign-on is convenient but presents a single point of failure that attackers may exploit.
Because an attacker may access apps that utilize a user’s SSO credentials, many security experts advise against utilizing social SSO services.
Apple launched its own single sign-on service as a more private alternative to Google, Facebook, LinkedIn, and Twitter. Sign in with Apple. The new service will restrict third-party data access. To enable Face ID and Touch ID on iOS devices, Apple’s SSO will require 2FA on all Apple ID accounts, increasing security.
Enterprise SSO
Password managers with client and server components are included in enterprise single sign-on (eSSO) software products and services. These password managers allow users to log in to target apps by replaying user credentials. These credentials are usually always a username and password, and target apps do not need to be updated in order for them to function with the eSSO system.
Advantages and disadvantages of SSO
One Sign-On allows customers to remember and manage fewer passwords and usernames for each application, which is one of the many advantages of using SSO.
- There is no need to input passwords, which makes logging on and utilizing programs much more streamlined.
- It reduces the likelihood of becoming a victim of phishing.
- As a result, fewer complaints or problems relating to passwords are received by IT support desks.
Disadvantages of SSO include the following:
- It does not address the specific degrees of security required for each application sign-on.
- In the event that availability is lost, users are prevented from accessing the many systems that are linked to the SSO.
- If unauthorised users can access the system, such individuals may be granted access to more than one application.
SSO vendors
SSO suppliers are well-known. Some provide extra services and SSO. SSO vendors:
- Avatier Identity Anywhere is a single sign-on solution (SSO) for systems built on Docker containers.
- Users are able to sign in to cloud apps from numerous devices thanks to Rippling’s capabilities.
- Single Sign-On (SSO) functionality is supported by the identity and access management (IAM) platform known as OneLogin, which is hosted in the cloud.
- Okta is a platform that offers single sign-on capabilities. Two-factor authentication is one of the features supported by Okta, which is used largely by corporate customers.
Benefits of single sign-on in healthcare
Does the healthcare organization you work for realize the value of products that just need one sign-on? Discover how to rapidly log in to various programs without much difficulty for people working in the healthcare industry.
Despite regulatory compliance issues, several healthcare businesses have used cloud services. Those services need more users to log in to many apps and systems in diverse contexts. This prompted IT organizations to search for identity management technologies that can handle cloud and on-premises authentication while boosting healthcare users’ security and efficiency.
Healthcare practitioners’ devices should be secured to safeguard patient data. Users may reduce data breaches by changing passwords regularly and making them complicated. Users must remember complicated passwords for various platforms, which is beneficial for security but difficult for users. Users often waste time logging in and changing passwords due to the number of password restrictions per application. Thus, healthcare has seen the advantages of single sign-on (SSO) systems grow. A healthcare SSO lets consumers use one account to enter several apps without remembering passwords.
Many application providers are now permitting identity federation, which means that not all authentication is completed by entering a username and password at a login page. This is the mechanism via which a single sign-on (SSO) may securely connect with an application in order to obtain a security token for a user and authenticate that user without having the user to manually submit their account information.
The benefits of single sign-on in healthcare
Single sign-on helps healthcare businesses beyond password consolidation and application login. SSOs improve user security. Many SSO solutions offer centralized identity management systems that allow IT organizations to manage users, enforce security standards, and monitor cloud account subscriptions. An IT staff may potentially freeze user accounts after too many failed login attempts, especially from a suspect external network.
Healthcare SSO products may report access logs centrally. That helps with HIPAA compliance and lets you see when and where users spend the most time.
Before choosing one, IT companies must examine how the best SSO systems will support cloud services, mobile users, and security. Medical institutions must estimate the long-term ROI of a healthcare SSO platform. According to critics, SSOs may reveal account data from numerous systems if compromised. SSOs reduce risks since non-SSO users repeat passwords for internal and external apps and keep them in insecure places.
Next Steps
New password manager threats might expose users’ data.
Healthcare providers want mobile device security
Healthcare security covers authentication and encryption.